No Copyright - Asked Permission from the author Alpha (@___0x00)
-___#ctfnepal #n3ph4ck Writeups, Solutions ___-
Nephack has been ended on Jan 7 . Congratulation to all the participants !!! Warning before reading this , please visit CTF Url and play there first.
So,till now there are 26 challenges available and only on some of them i have authority to do blog. Later on other challenges solutions, writeups, ctfnews will be posted on 0xctf.blogspot.com \ ;)
CTF URL: ctf2018.cynicaltechnology.com.np
Skip this part, if you’re here just for writeup
Contest Information
- The registration link is available on Jan5/Jan 6 on the event date at IT Park.
- Registration Charge is Rs. 250 per person.
- Contest will be available only for 2 days , ie. Jan 5 & 6.
- Solving each problem will get certain points. Winners will be ranked by points.If the points are the same, the winners will be ranked by time of the last correct submission.
- Flag format: cynical_flag{Secret-Key}
- Game makers and staffs will not be counted in the ranking process.
Contest Rules
During the contest, any of the following behaviors will lead to the disqualifications :
- Any behavior that compromises the fairness of contest
- Publishing, exchanging problem solutions
- Attacking any personal, including participants and non-participants, or the contest system itself.
- One team can only have max of 3 player.
- Each player can only join one team.
Stop the talk, lets begin to read
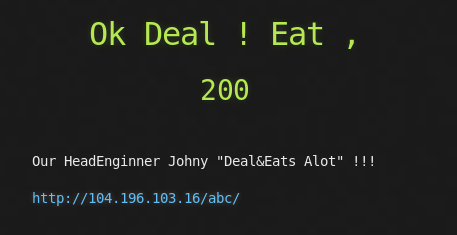
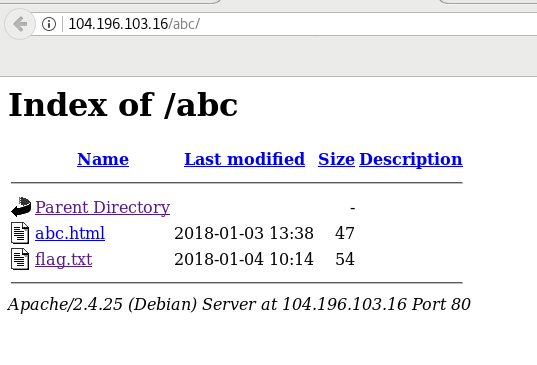
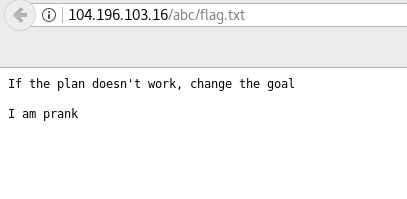
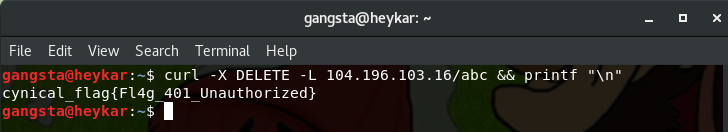
1. Ok Deal ! Eat , (200)
Just looking at the hints and title, i guess you would probably solve it easily, HeadEnginner = HeadEr , Deal & Eat = DELETE
Without any delay, just change the HTTP request header methods to DELETE,
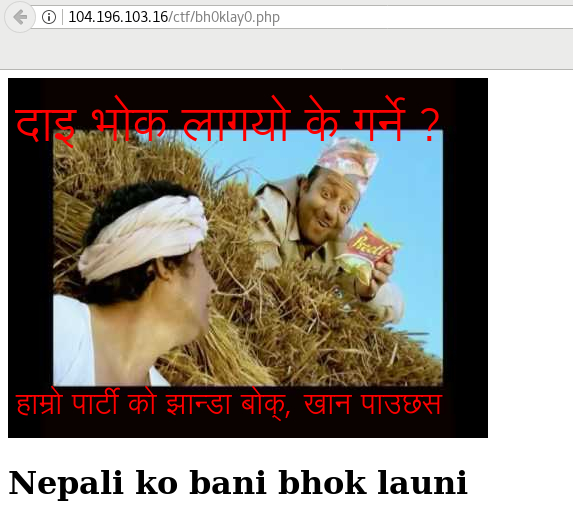
2. Someone’s Hungry! (300)
Notice that icon image, what’s inside that ?
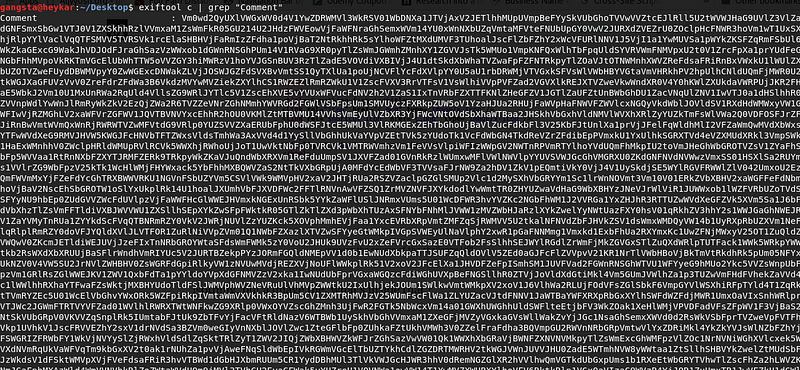
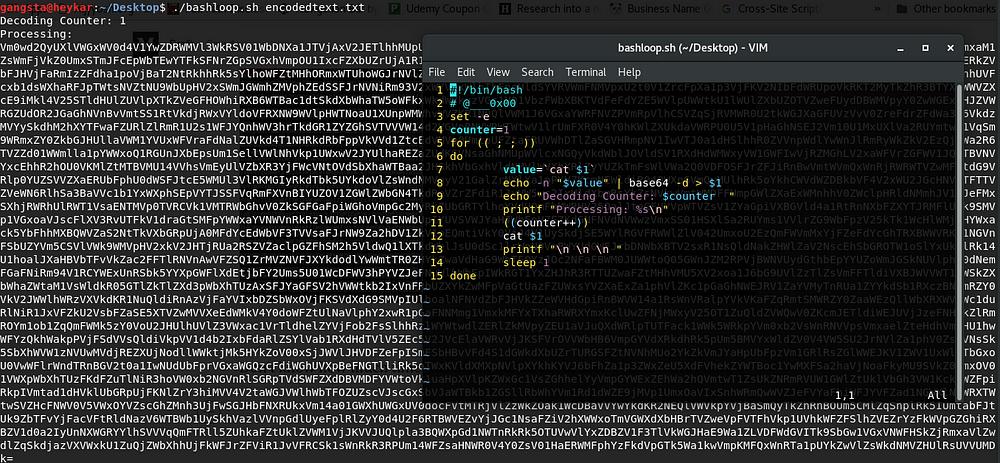
Don’t know how much time this might be encoded, bash comes handy here !
Hungry huH ? c00KIE ?
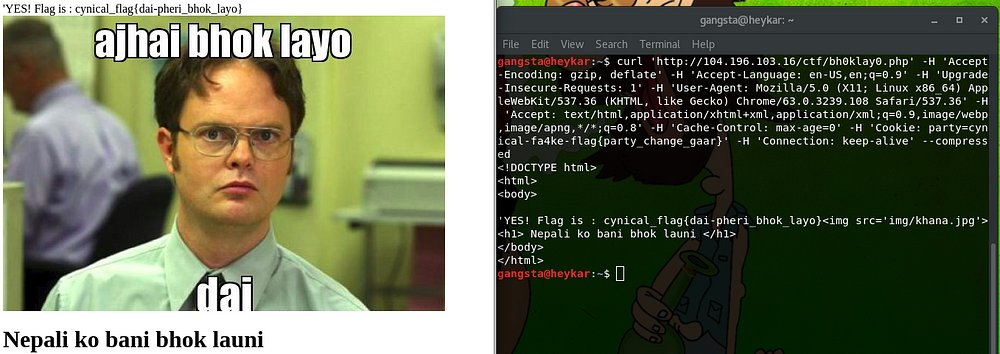
curl ‘http://104.196.103.16/ctf/bh0klay0.php' -H ‘Accept-Encoding: gzip, deflate’ -H ‘Accept-Language: en-US,en;q=0.9’ -H ‘Upgrade-Insecure-Requests: 1’ -H ‘User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/63.0.3239.108 Safari/537.36’ -H ‘Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8’ -H ‘Cache-Control: max-age=0’ -H ‘Cookie: party=JTU5JTMzJTZjJTc1JTYxJTU3JTRlJTY4JTYyJTQzJTMxJTZkJTU5JTU0JTUyJTcyJTVhJTUzJTMxJTZkJTYyJTQ3JTQ2JTZlJTY1JTMzJTQyJTY4JTYzJTZlJTUyJTM1JTU4JTMyJTRlJTZmJTU5JTU3JTM1JTZlJTVhJTU2JTM5JTZlJTU5JTU3JTQ2JTc5JTY2JTUx’ -H ‘Connection: keep-alive’ — compressed
Cookie : party = some encoded text ,
After Base64 Decoding :
%59%33%6c%75%61%57%4e%68%62%43%31%6d%59%54%52%72%5a%53%31%6d%62%47%46%6e%65%33%42%68%63%6e%52%35%58%32%4e%6f%59%57%35%6e%5a%56%39%6e%59%57%46%79%66%51
After Url Decoding:
Y3luaWNhbC1mYTRrZS1mbGFne3BhcnR5X2NoYW5nZV9nYWFyfQ
After Base64 Decoding:
:¼ þ;Å%Ÿ
Adding 2 equals ( == ), Y3luaWNhbC1mYTRrZS1mbGFne3BhcnR5X2NoYW5nZV9nYWFyfQ==
After Base64 Decoding:
cynical-fa4ke-flag{party_change_gaar}
Changing Cookie : party = cynical-fa4ke-flag{party_change_gaar}
3. UFO: Alien Invasion (300)
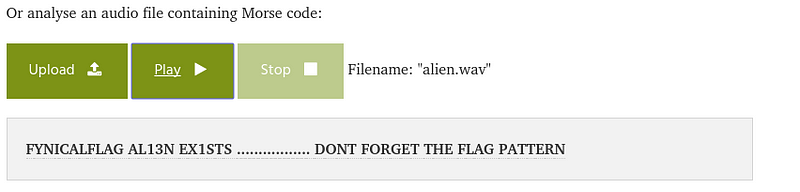
Not a Steg challenge this is, you could hear DITS AND DATS from audio file , might be Morse Code ?
Morse Code : Audio Decoder https://morsecode.scphillips.com/labs/audio-decoder-adaptive/
4. Dig Deeper Deeeeeper (400)
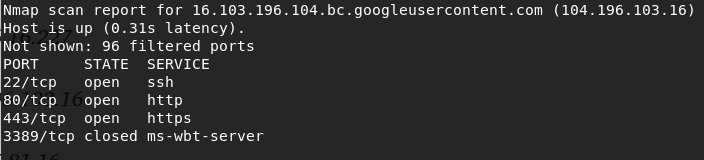
From web challenges, you could collect 3 IP Address
35.196.16.227
104.196.103.16
35.185.81.16
Do Port Scan
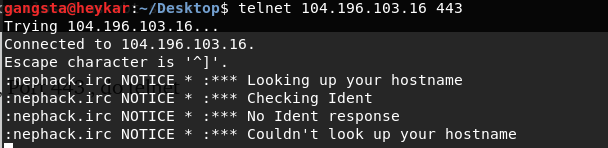
Notice Port 443 , do telnet
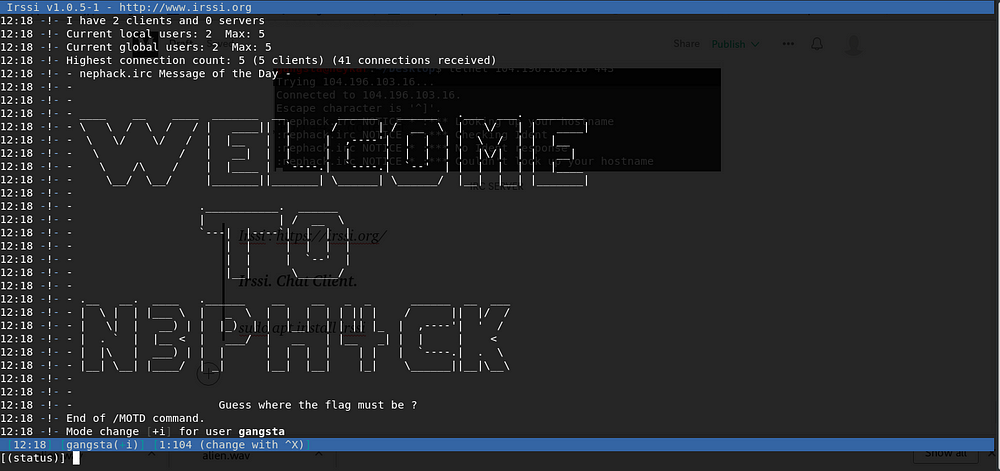
Irssi : https://irssi.org/
Irssi. Chat Client.
sudo apt install irssi
/admin
Administrative info about nephack.irc
12:xx -!- Join channels for flag
12:xx -!- Main Server Administrator
12:xx -!- <root@m4f1a>
/list
Channel Users Name
12:20 -!- #z3r0Xflag 1 [+nt]
63796e6963616c5f666c61677b77335f6c61765f72336c6179636834747d
12:20 -!- #ZEROxthisisflag 1 [+nt]
12:20 -!- #cynical 1 [+nt]
12:20 -!- #flag 1 [+nt]
12:20 -!- End of /LIST
Topic for #z3r0Xflag:
63796e6963616c5f666c61677b77335f6c61765f72336c6179636834747d
0x63796e6963616c5f666c61677b77335f6c61765f72336c6179636834747d
After Decoding hex
FLAG: cynical_flag{w3_lav_r3laych4t}
5. Broken Image (200)
gimp -c brokenimage
(gimp:21326): GLib-GObject-WARNING **: g_object_set_is_valid_property: object class ‘GeglConfig’ has no property named ‘cache-size’
GIMP-Error: Opening ‘/home/gangsta/Downloads/brokenimage’ failed: Unknown file type
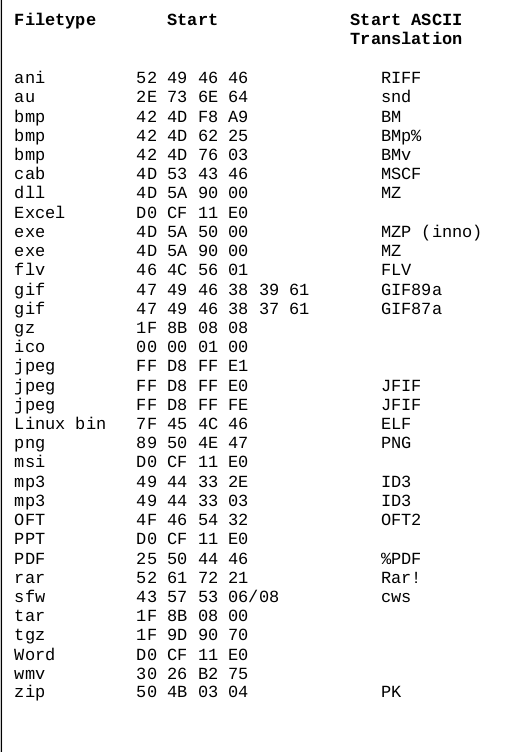
What could be web images most made of ? Obviously, JPEG || PNG
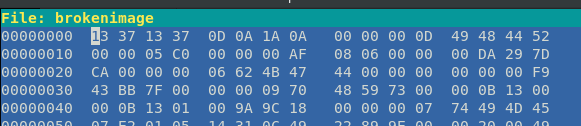
cat, file, strings won’t help you here, Do hexdump
File headers are used to identify a file by examining the first 4 or 5 bytes of its
hexadecimal content.
Save the image and open with any Image viewer you will get the flag
6. Hail Kim Jong-un (100)
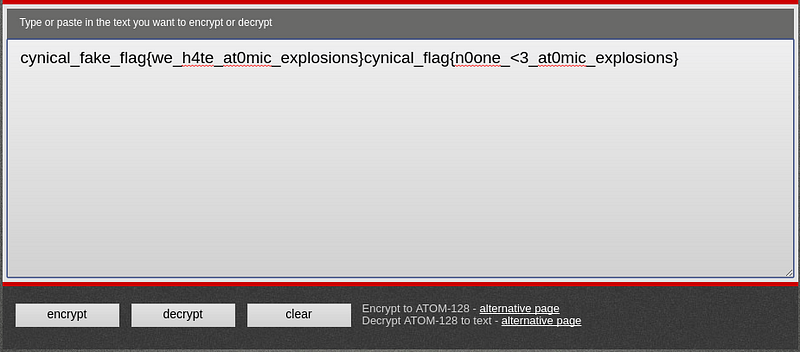
Km6VMiTX+hcxKi96jlL3Kin6TJQmLHczToA6jlhJSIkBKkc6po13+mTB+lutQf0GKm6VMiTX+hcx+IhyQf02+41a+xHFQfT8SkcX0819MiTFLjXq+IctMicVnsgmA/CC
This is nothing, just a ATOM-128 Encoding. Use any decrypter you’ll love to use. My recommendation :
7. Wanna Die (200)
What’s that .enc file be ? Openssl enc’d data with salted password
gangsta@heykar:~/Downloads$ file crypto.enc
crypto.enc: openssl enc’d data with salted password
Google, how to decrypt enc file from openssl, asks password while decrypting.Password is : nephack
gangsta@heykar:~$ openssl enc -help
gangsta@heykar:~$ openssl enc -ciphers
Ciphers used in this file : aes-128-cbc
Block ciphers operate on a fixed length string of bits. The length of this bit string is the block size. Both the input (plaintext) and output (ciphertext) are the same length; the output cannot be shorter than the input
gangsta@heykar:~/Downloads$ openssl enc -d -aes-128-cbc -in crypto.enc -out flag.txt
enter aes-128-cbc decryption password: nephack
gangsta@heykar:~/Downloads$ cat flag.txt
cynical_flag{b4d_crypt0}
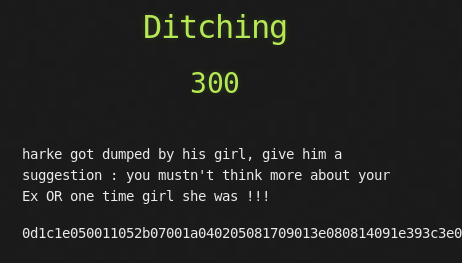
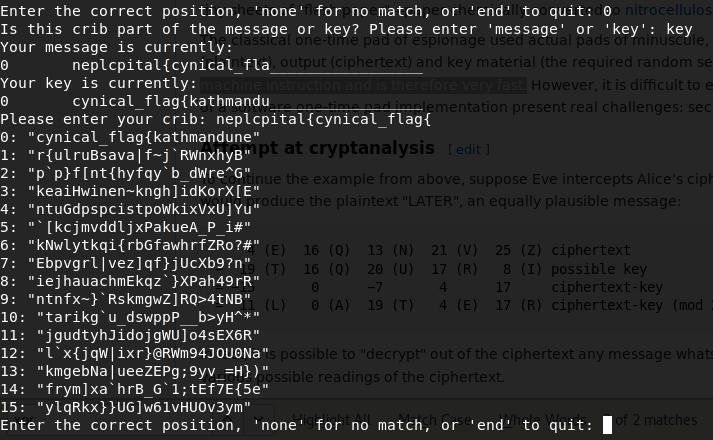
8. Ditching (300)
0d1c1e050011052b07001a040205081709013e080814091e393c3e0e585815293951291a521e16
Have some read first :
In cryptography, the one-time pad (OTP) is an encryption technique that cannot be cracked, but requires the use of a one-time pre-shared key the same size as, or longer than, the message being sent.
The one-time pad was re-invented in 1917. XOR operation can be used for the encryption of a one-time pad. The XOR operation is often used to combine the plain text and the key elements, and is especially attractive on computers since it is usually a native machine instruction and is therefore very fast.
Dig more and more !!!
https://www.youtube.com/watch?v=FlIG3TvQCBQ
https://www.khanacademy.org/computing/computer-science/cryptography/ciphers/a/xor-bitwise-operation
https://en.wikipedia.org/wiki/One-time_pad
https://security.stackexchange.com/questions/20941/how-can-i-decode-a-message-that-was-encrypted-with-a-one-time-pad
http://travisdazell.blogspot.com/2012/11/many-time-pad-attack-crib-drag.html
Looking at title,message and hints you could have some idea that it may be some one time pad encryption with XOR.
Crib Dragging attack can be used to crypt analyze One-Time Pad with reused key (XOR two cipher texts together).
cribdrag — an interactive crib dragging tool for cryptanalysis on ciphertext generated with reused or predictable stream cipher keys.
https://github.com/SpiderLabs/cribdrag
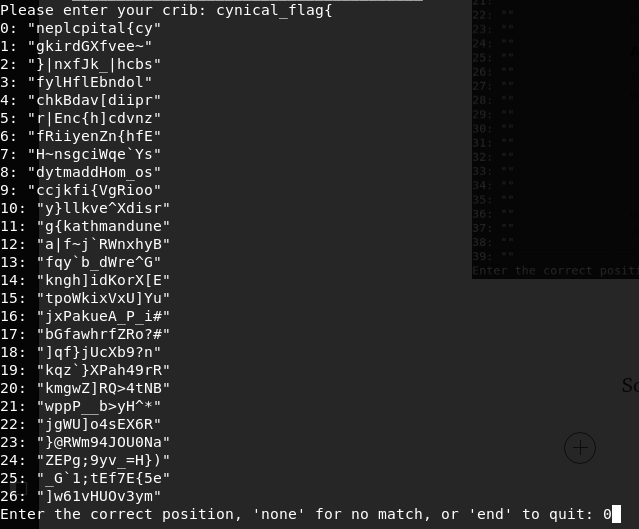
So, we already mention the flag pattern, type cynical_flag{ at crib
The first one looked like a valid key.
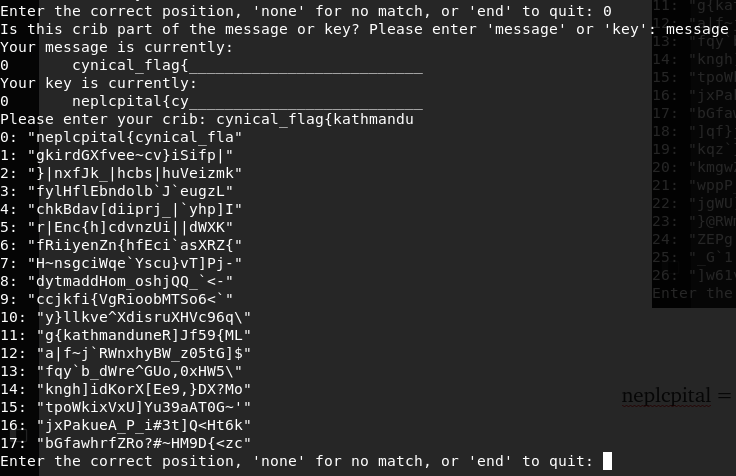
neplcpital = kathmandu , put cynical_flag{kathmandu in message
that’s like flag pattern again , changing crib part and enterning crib neplcpital{cynical_flag{
kathmandune , what’s ne ? Guess the word : if you’re guessing nephackinstead of nepal , salute _/\_
crib : cynical_flag{kathmandunephack
Flag: cynical_flag{IT_m33t_k4vr3}
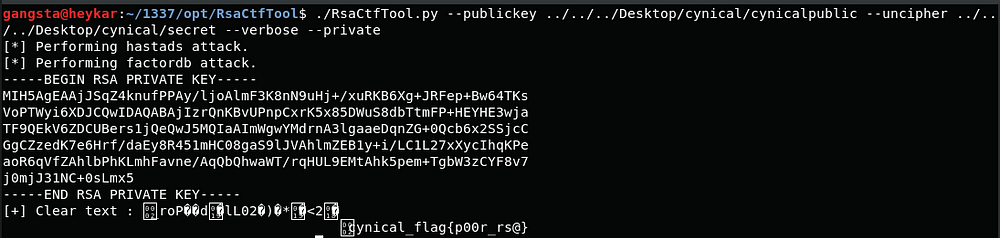
9. Privacy WAR (300)
cynicalsecret.zip contains public key and a encrypted file
gangsta@heykar:~$ openssl rsa -inform PEM -text -noout -pubin < cynicalpublic
Public-Key: (399 bit)
Modulus:
52:a9:9e:24:9e:e7:cf:3c:0c:bf:96:3a:00:96:61:
77:2b:c9:cd:f6:e1:e3:fb:fc:6e:44:a0:7a:5e:0f:
89:44:57:a9:f8:1c:3a:e1:32:ac:56:83:d3:5b:28:
ba:5c:32:42:43
Exponent: 65537 (0x10001)
Either you could solve this challenge by converting this hex to decimal and factorize, get prime numbers ,export private key using python tools, libraries
OR
Clone this tool,
https://github.com/Ganapati/RsaCtfTool
RSA tool for ctf — retreive private key from weak public key and/or uncipher data
./RsaCtfTool.py — publickey ../keyhere — uncipher ../filehere — verbose — private
10. Don’t trust the logs (100)
Download the log, do cat | grep “flag” or grep “{“
plavpny_synt{jryy_v_ybir_ubj_lbh_fbyir} — ROT13
gangsta@heykar:~/Downloads$ echo “plavpny_synt{jryy_v_ybir_ubj_lbh_fbyir}” | tr ‘[A-Za-z]’ ‘[N-ZA-Mn-za-m]’
cynical_flag{well_i_love_how_you_solve}
Author: Alpha Bro
Greetz to them : @___0x00 ,@nlamgade , cynical technology, m4f1a, it park nepal , rootnep.al






















No comments:
Post a Comment